Our patent-protected systems and methods have been consolidated for ease of review. Reference numbers have been inserted for direct referral to our sample software solution video clips and screendumps demonstrating how the methods may be implemented. The intellectual property may be embodied in different ways within alternative products and the provision of our video clips serves only as an indication of how the methods may be provided to clients. Where you are seeking to eliminate risks to your organization from direct or indirect patent infringement litigation, we advise you to consult with your Office of the General Counsel/legal department and Chief Risk Officer. If in doubt, compare our patents with those of our competitors and the priority dates for each company.
PATENT CLAIMS & DRAWINGS
The following text provides Quantar’s patented methods. The accompanying drawings are provided for reference and do not align with the paragraphs alongside (Click to Open). They should be reviewed for each set of claims. Our emphasis has been added to the relevant wording for ease of mapping between methods and the implemented methods within our software, demonstrating functionality for a user.
APPLICATION SCREENDUMPS (Click to Open in New Window)
12/811,208 Assessing threat to at least one computer network (2010)
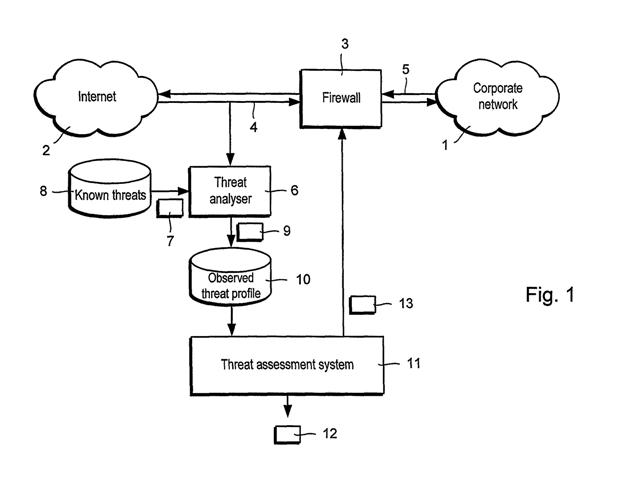
1. Apparatus (C1; C2) for assessing threat to at least one computer network, the threat including at least one electronic threat, the computer network comprising a plurality of IT systems and a plurality of business processes operating on the plurality of IT systems, wherein (a) at least one IT system has two or more of the plurality of business processes operating thereon or (b) at least one business process operates on two or more of the plurality of IT systems, (C3) (B6; B7) the apparatus comprising at least one processor and a memory coupled to the processor, the memory storing instructions executable by the processor (C4) that cause the processor to:
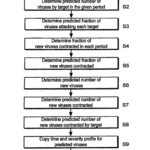
predict future threat activity based on past observed threat activity (C5A) (B11; B9; B14; B17) including, for the at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target, (C5A) (B1; B12)
determine expected downtime of each system (C6) of the plurality of IT systems in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency, (C5A) (B7; B10)
determine loss for each of the plurality of business processes dependent on the downtimes of the IT systems, (C7) (B12) and
add losses for the plurality of business processes so as to obtain a combined loss arising from the threat activity. (C7) (B9; B11; B15; B17)
add losses for the plurality of business processes so as to obtain a combined loss arising from the threat activity. (C7) (B9; B11; B15; B17)
2. The apparatus according to claim 1, wherein the instructions comprise:
a first module configured to determine the predicted threat activity including, for the at least one electronic threat, (C1) (B2; B17) to receive observed threat data from a database, (C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
a second module configured to determine the expected downtime of each IT system (C6) of the plurality of IT systems in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (B7; B10) and
a third module configured to determine the loss for each of a plurality of business processes. (C6 C7) (B7; B10)
3. The apparatus according to claim 2, wherein the third module is configured to add the losses for the plurality of business processes. (C7) (B9; B11; B15; B17)
4. The apparatus according to claim 1, wherein the apparatus is further configured to store at least one of the losses and the combined loss in a storage device. (C3)
5. The apparatus according to claim 1, wherein the apparatus is configured to display at least one of the losses and the combined loss on a display device. (C2; C4)
6. The apparatus according to claim 1, further configured to output the predicted threat activity to a firewall. (C2) (B2)
7. The apparatus according to claim 1, wherein loss is value at risk. (B11; B15)
8. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying at least one system. (C2) (B1)
9. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying frequency of occurrence of the threat. (C5B) (B1)
10. The apparatus according to claim 9, wherein the frequency of occurrence of the threat includes at least one period of time and corresponding frequency of occurrence for the at least one period of time.(C5B) (B1; B4; B14; B16)
11. The apparatus according to claim 1 wherein the plurality of IT systems include a plurality of software systems. (C3) (B6)
12. A method of assessing threat to at least one computer network, (C1 – C7) the threat including at least one electronic threat, the network comprising a plurality of IT systems wherein a plurality of business processes operate on the plurality of IT systems, and wherein (a) at least one IT system has two or more of the plurality of business processes operating thereon or (b) at least one business process operates on two or more of the plurality of IT systems, (C3) (B6; B7) the method comprising, by using at least one computer processor:
predicting threat activity based on past observed activity (C5A) (B11; B9; B14; B17) including, for the at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B2)
determining expected downtime of the plurality of IT systems (C6) in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determining loss for the plurality of business processes dependent on the downtimes of the IT systems; (C7) (B12)
adding losses for the plurality of business processes to obtain a combined loss arising from the threat activity. (C7) (B9; B11; B15; B17)
13. The method according to claim 12, further comprising:
storing at least one of the losses and combined loss in a storage device. (C5B)
14. The method according to claim 12, further comprising:
displaying at least one of the losses and combined loss on a display device.(C4)
15. A non-transitory computer readable medium storing a computer program which when executed by a computer system, causes the computer system to perform a method of assessing threat to at least one computer network, (C1; C2) the threat including at least one electronic threat, the computer network comprising a plurality of IT systems wherein a plurality of business processes operate on the plurality of IT systems, and wherein (a) at least one IT system has two or more of the plurality of business processes operating thereon or (b) at least one business process operates on two or more of the plurality of IT systems, (C3) (B6; B7) the method comprising:
predicting threat activity based on past observed activity (C5A) (B9; B11; B14; B17) including, for the at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determining expected downtime of each of the plurality of IT systems (C6) in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determining loss for the plurality of business processes (C7) (B12) dependent on the downtimes of the IT systems;
adding losses for the plurality of business processes to obtain a combined loss arising from the threat activity. (C7) (B9; B11; B15; B17)
14/827,712 Assessing Threat to at Least One Computer Network 2015
1. Apparatus for assessing and valuing computer network threats, (C1; C2) the threats including at least one electronic threat, the computer network comprising a plurality of IT systems and a plurality of business processes operating on the plurality of IT systems, (C3) (B6; B7) the apparatus comprising at least one processor and a memory coupled to the processor, (C4) the memory storing instructions executable by the processor that cause the processor to:
predict future threat activity based on past observed threat activity (C5A) (B9; B11; B14; B17) including, at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5B) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats (C1) and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determine expected downtime of each system of the plurality of IT systems in dependence upon said predicted threat activity (C6) including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determine the financial loss for each of the plurality of business processes dependent on the downtimes of the IT systems, (C7) (B12) and;
add the financial losses for the plurality of business processes so as to obtain a combined financial loss arising from the threat activity (C7) (B9; B11; B15; B17).
2. The apparatus according to claim 1, wherein the instructions comprise:
a first module configured to determine the predicted threat activity (C1) (B2; B17) including, at least one electronic threat, to receive observed threat data from a database, (C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
a second module configured to determine the expected downtime of each IT system (C6) of the plurality of IT systems in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency (C5A) (B7; B10) and;
a third module configured to determine the financial loss for each of a plurality of business processes. (C6? C7?) (B7; B10)
3. The apparatus according to claim 2, wherein the third module is configured to add the financial losses for the plurality of business processes. (C7) (B9; B11; B15; B17)
4. The apparatus according to claim 1, wherein the apparatus is further configured to store at least one of the financial losses and the combined financial loss in a storage device. (C3)
5. The apparatus according to claim 1, wherein the apparatus is further configured to output the financial losses and the combined financial loss to other apparatus comprising at least one processor and a memory coupled to the processor, the memory storing instructions being executable by the processor. (C4)
6. The apparatus according to claim 1, wherein the apparatus is configured to display at least one of the financial losses and the combined financial loss on a display device. (C4)
7. The apparatus according to claim 1, further configured to output the predicted future event activity to a firewall. (C2) (B2)
8. The apparatus according to claim 1, further configured to output the profile of predicted threat activity to a firewall. (C2) (B2)
9. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying at least one system. (C2)
10. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying frequency of occurrence of the threat. (C5B) (B1)
11. The apparatus according to claim 10, wherein the frequency of occurrence of the threat includes at least one period of time and corresponding frequency of occurrence for the at least one period of time. (C5B) (B1; B4; B14; B16)
12. The apparatus according to claim 1 wherein the plurality of IT systems include a plurality of software systems. (C3) (B6)
13. A method of assessing and valuing computer network threats, (C1 – C7) the threats including at least one electronic threat, the network comprising a plurality of IT systems wherein a plurality of business processes operate on the plurality of IT systems (C3) the method comprising, by using at least one computer processor:
predicting threat activity based on past observed activity (C5A) (B2; B4; B14; B16) including, for at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14); B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determining expected downtime of the plurality of IT systems (C6) in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determining the financial loss for the plurality of business processes (C7) (B12) dependent on the downtimes of the IT systems;
adding the financial losses for the plurality of business processes to obtain a combined financial loss arising from the threat activity. (C7) (B9; B11; B15; B17)
14. The method according to claim 13, further comprising;
storing at least one of the financial losses and the combined financial loss in a storage device. (C5B)
15. The method according to claim 13, further comprising;
displaying at least one of the financial losses and the combined financial loss on a display device. (C4) (B3; B12; B15; B17)
16. A non-transitory computer readable medium storing a computer program which when executed by a computer system, causes the computer system to perform a method of assessing and valuing computer network threats, (C2) the threats including at least one electronic threat, the computer network comprising a plurality of IT systems wherein a plurality of business processes operate on the plurality of IT systems (C3) (B6; B7), the method comprising:
predicting threat activity based on past observed activity including, at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) ((B1; B2)
determining expected downtime of each of the plurality of IT systems (C6) in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determining the financial loss for the plurality of business processes dependent on the downtimes of the IT systems; (C7) (B12)
adding the financial losses for the plurality of business processes to obtain a combined financial loss arising from the threat activity. (C7) (B9; B11: B15; B17)
15/017,645 Apparatus and method for assessing financial loss from threats capable of affecting at least one computer network 2016
1. Apparatus for assessing financial loss from threats capable of affecting at least one computer network, (C1; C2) a network includes a plurality of interconnected networks, the threats including at least one electronic threat, the computer network comprising a plurality of IT systems, an IT system defined in terms of physical location, (B12) and a plurality of operational business processes operating on the plurality of IT systems, (C3) (B6; B7) the apparatus including one or more computer processors and a computer readable memory in which programming code is stored, (C4) wherein the one or more computer processors are configured pursuant to programming code in the computer readable memory to,
predict for each of a plurality of threats capable of affecting at least one computer network in which a plurality of systems operate, future threat activity based on past observed threat activity (C5A) (B9; B11; B14; B17) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses, Trojan horses, computer worms, hacking and denial of service attacks, (C2) (B1; B4; B14; B16) to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future threat event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determine expected downtime of each system (C6) of the plurality of IT systems independence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determine financial loss for each of the plurality of operational business processes (C7) (B12) dependent on the downtimes of the IT systems;
add financial losses for the plurality of business processes to obtain a combined financial loss arising from the threat activity. (C7) (B9; B11; B15; B17)
2. The apparatus according to claim 1, wherein the instructions comprise:
a first module configured to determine the predicted threat activity (C2) (B2; B17) including for the at least one electronic threat, to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
a second module configured to determine the expected downtime of each IT system (C6) of the plurality of IT systems in dependence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10) and
a third module configured to determine the loss for each of a plurality of business processes. (C6 C7) (B7; B10)
3. The apparatus according to claim 2, wherein the third module is configured to add the financial losses for the plurality of business processes. (C7) (B9; B11; B15; B17)
4. The apparatus according to claim 1, wherein the apparatus is further configured to store at least one of the financial losses and the combined financial loss in a storage device. (C3)
5. The apparatus according to claim 1, wherein the apparatus is configured to display at least one of the financial losses and the combined financial loss on a display device. (C2; C4)
6. The apparatus according to claim 1, further configured to output the predicted threat activity to a firewall. (C2) (B2)
7. The apparatus according to claim 1, wherein loss is expressed as value at risk; (B11; B15)
expected financial loss; (B3; B11; B15; B17)
quantified financial loss from disabled business processes; (B3; B11; B15; B17)
a priori organizational financial loss exposure. (B3; B11; B15; B17)
8. The apparatus according to claim 1, further configured to output a report of at least one of the predicted financial losses and the combined financial loss.
9. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying at least one system. (C2) (B1; B7)
10. The apparatus according to claim 1, wherein the observed list of threats includes, for each threat, information identifying frequency of occurrence of the threat. (C5B) (B1; B4; B8)
11. The apparatus according to claim 10, wherein the frequency of occurrence of the threat includes at least one period of time and corresponding frequency of occurrence for the at least one period of time. (C5B) (B1; B2; B4; B8; B14; B16)
12. The apparatus according to claim 1 wherein the plurality of IT systems include software systems, hardware systems, or a combination thereof. (C3) (B6)
13. A method for assessing financial loss from threats capable of affecting at least one computer network, (C1 – C7) a network includes a plurality of interconnected networks, the threats including at least one electronic threat, the computer network comprising a plurality of IT systems, (B6) an IT system defined in terms of physical location, (B12) and a plurality of operational business processes operating on the plurality of IT systems, (C3) (B6; B3; B10) the apparatus including one or more computer processors and a computer readable memory in which programming code is stored, (C4) wherein the one or more computer processors are configured pursuant to programming code in the computer readable memory to,
predict for each of a plurality of threats capable of affecting at least one computer network in which a plurality of systems operate, future threat activity based on past observed threat activity (C5A) (B9; B11; B14; B17) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses, Trojan horses, computer worms, hacking and denial of service attacks, (C2) (B1; B2; B14; B16) to receive observed threat data from a database, (CC1; C2) (B1; B2; B14; B16) to extrapolate future threat event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determine expected downtime of each system (C6) of the plurality of IT systems independence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determine financial loss for each of the plurality of operational business processes (C7) dependent on the downtimes of the IT systems; (B12)
add financial losses for the plurality of business processes to obtain a combined financial loss arising from the threat activity. (C7) (B9; B11; B15; B17)
14. The method according to claim 13, further comprising:
storing at least one of the financial losses: and combined financial loss in a storage device. (C5B)
15. The method according to claim 13, further comprising:
displaying at least one of the financial losses and combined financial on a display device. (C4) (B3; B11; B15; B17)
16. A non-transitory computer readable memory storing a computer program which when executed by a computer system, causes the computer system to perform a method of assessing financial loss from threats capable of affecting at least one computer network, (C1 – C7) a network include a plurality of interconnected networks, the threats including at least one electronic threat, the computer network comprising a plurality of IT systems, (B6) an IT system defined in terms of physical location, (B12) and a plurality of operational business processes operating on the plurality of IT systems, (C2) (B6; B3; B10) the method comprising:
predict for each of a plurality of threats capable of affecting at least one computer network in which a plurality of systems operate, future threat activity based on past observed threat activity (C5A) (B9; B11; B14; B17) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses, Trojan horses, computer worms, hacking and denial of service attacks, (B1; B2; B14; B16) to receive observed threat data from a database, (C1; C2) (B1; B2; B14; B16) to extrapolate future threat event frequency (C5A) and to produce a profile of predicted threat activity, (C5A) wherein the observed threat data includes observed threats and, for each observed threat, one or more targets for the observed threat and a severity score for each target; (C5A) (B1; B12)
determine expected downtime of each system of the plurality of IT systems (C6) independence upon said predicted threat activity including the severity scores and extrapolated future event frequency; (C5A) (B7; B10)
determine financial loss for each of the plurality of operational business processes (C7) dependent on the downtimes of the IT systems; (B12)
add financial losses for the plurality of business processes to obtain a combined financial loss arising from the threat activity. (C7) (B9; B11; B15; B17)
13/322,298 Assessing threat to at least one computer network 2011
1. An apparatus including one or more computer processors and a non-transient computer readable memory, (C4) wherein the one or more computer processors are configured pursuant to
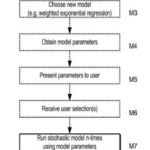
programming code in a the non-transient computer readable memory to predict, for each of a plurality of threats capable of affecting at least one computer network in which a plurality of systems operate, future threat activity (B9; B11; B14; B17) using a Monte Carlo method based on stochastic modelling of past observed threat events, (A6) (B15; B18)
wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses, wherein the one or more computer processors are configured, for a given threat, to model a set of past observed threat events (B14; B16) to obtain an estimate of at least one model parameter, and, in a Monte Carlo simulation of a given threat, (A6; A9)
to predict future threat events using the at least one model parameter and a stochastic model (A6) (B18) using a projection of at least one model parameter which is based on the estimate of at least one model parameter and on a randomly-drawn variable, and to predict a distribution of future threat events by repeating the simulation using a plurality of variables; (A6) (B17) and
wherein the apparatus is further configured to determine an expected downtime of each of said systems (A7) (B7; B10) in dependence upon said predicted future threat activity and to determine a financial loss for each of a plurality of operational processes (A7) (B12) dependent on the downtimes of each of said systems and to add the financial losses for said plurality of processes so as to obtain a combined financial loss arising from the predicted future threat activity. (A8) (B9; B11; B15; B17)
2. The apparatus according to claim 1, wherein the apparatus is configured to model a set of past observed threat events so as to obtain at least one model parameter. (A6) (B15)
3. The apparatus according to claim 2, wherein the apparatus is configured to model the set of past observed threat events using regression. (A6)
4. The apparatus according to claim 3, wherein the apparatus is configured to model the set of past observed threat events using weighted regression. (A6) (B15; B17)
5. The apparatus according to claim 4, wherein the apparatus is configured to model the set of past observed threat events using linear regression. (A6) (B11)
6. The apparatus according to claim 5, wherein the apparatus is configured to model the set of past observed threat events using exponential regression. (A6) (B15)
7. The apparatus according to claim 6, wherein the apparatus is configured to model the set of past observed threat events using at least two different models and to obtain at least two different sets of model parameters. (A6) (B18)
8. The apparatus according to claim 7, wherein at least one model parameter includes at least one parameter indicating goodness of fit of the model.
9. The apparatus according to claim 1, further comprising a user interface which is configured to present at least one model parameter to a user. (A6)
10. The apparatus according to claim 1, wherein the apparatus is configured to predict future threat events using at least one model parameter and a stochastic model using said at least one model parameter. (A6) (B17)
11. The apparatus according to claim 10, wherein the apparatus is configured to randomly draw at least one variable according to a predefined distribution and to use said at least one variable in the stochastic model. (A6)
12. The apparatus according to claim 11, wherein the apparatus is configured to predict a distribution of future threat events using a Monte Carlo method by repeating a simulation. (A6) (B15; B17)
13. The apparatus according to claim 1, wherein the apparatus is configured to allow for parameter uncertainty.
14. The apparatus according to claim 1, further comprising a user interface which is configured to present an outcome of stochastic modelling to a user. (A6)
15. The apparatus according to claim 1, wherein the apparatus is configured to store at least one of the losses and the combined loss in a storage device. (A6)
16. The apparatus according to claim 1, wherein the apparatus is configured to display at least one of the losses and the combined loss on a display device.(A6)
17. The apparatus according to claim 1, wherein the apparatus is configured to retrieve a list of past observed threats (A1; A2) (B19) and to determine the predicted future threat activity (A5A) (B4; B11; B17) based upon the list of past observed threats.
18. The apparatus according to claim 17, wherein the past observed list of threats includes, for each threat, information identifying at least one system. (A2) (B1; B5; B6)
19. The apparatus according to claim 17, wherein the past observed list of threats includes, for each threat, information identifying frequency of occurrence of the threat. (A5A; A5B) (B1; B4; B8; B14; B16)
20. The apparatus according to claim 19, wherein the frequency of occurrence of the past observed threat includes at least one period of time and corresponding frequency of occurrence for the at least one period of time. (C5B)(A5A; A5B) (B1; B4; B14; B16)
21. The apparatus according to claim 1, wherein the plurality of systems include a plurality of software systems. (A3) (B6)
22. The apparatus according to claim 1, comprising:
at least one computer system,
wherein the or each computer system comprises at least one processor and at least one memory. (A4)
23. The apparatus according to claim 1, wherein loss is value at risk. (B11)
24. The apparatus according to claim 1, wherein the one or more processors is configured pursuant to programming code to provide at least two modules including a first module configured to predict future threat activity using a Monte Carlo method (A6) (B15; B18) and to output the predicted future threat activity to a second module. (A4)
25. A computer-implemented method, the method being performed by a computer system having one or more computer processors and a non-transient computer readable memory, (A4) the one or more computer processors being configured pursuant to programming code in the non-transient computer readable memory, the method comprising: predicting, for each of a plurality of threats, future threat activity using a Monte Carlo method based on stochastic modelling of past observed threat events (A6) (B15; B18) capable of affecting at least one computer network in which a plurality of systems operate,
wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses; (A1; A2) (B1; B4; B14; B16)
wherein for each given threat the method comprises: modelling a set of past observed threat events to obtain an estimate of at least one model parameter; (A6)
performing a Monte Carlo simulation of the given threat by: predicting future threat events using the at least one model parameter and a stochastic model using a projection of at least one model parameter which is based on the estimate of at least one model parameter and on a randomly-drawn variable, and predicting a distribution of future threat events by repeating the simulation using a plurality of variables; and (A6) (B15; B17)
wherein determining an expected downtime of each system (A7) in dependence upon said predicted future threat activity; (B7; B10)
determining a financial loss for each of a plurality of operational processes (A7) dependent on the downtimes of the systems; (B12)
adding the financial losses for the plurality of processes to obtain a combined financial loss (A8) arising from the future threat activity. (B9; B11; B15; B17)
26. The method according to claim 25, wherein the predicting threat activity based on stochastic modelling (A6) of past observed threat events comprises:
modelling a set of past observed threat events so as to obtain at least one model parameter. (A6)
27. The method according to claim 25, wherein the predicting future threat activity based on stochastic modelling of past observed threat events includes:
predicting future threat events using at least one model parameter and a stochastic model using said at least one model parameter. (A6) (B16)
28. The method of claim 25, in which the computer system includes at least two modules, wherein the method further comprises:
using a first module to predict future threat activity and to output the predicted future threat activity to a second module. (A4)
29. A non-transitory computer readable medium having a computer program thereon, which when executed by a computer system having one or more computer processors and a non-transient computer readable memory, causes the computer system to predict, for each of a plurality of threats, future threat activity (B9; B11; B14; B17) a Monte Carlo method based on stochastic modelling of past observed threat events (A6) (B15; B18) capable of affecting at least one computer network in which a plurality of systems operate, (A2) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses;
wherein execution of the computer program causes the computer system to perform, for each given threat, steps comprising:
modelling a set of past observed threat events to obtain an estimate of at least one model parameter; (A6) (B15)
performing a Monte Carlo simulation of the given threat by: (A6) (B15; B18)
predicting future threat events using the at least one model parameter and a stochastic model using a projection of at least one model parameter which is based on the estimate of at least one model parameter and on a randomly-drawn variable, and predicting a distribution of future threat events by repeating the simulation using a plurality of variables; and (A6; A9) (B4; B11; B17)
wherein determining an expected downtime of each system (A7) (B7; B10) in dependence upon said predicted future threat activity;
determining a financial loss for each of a plurality of operational processes (A7) dependent on the downtimes of the systems; (B12)
adding the financial losses for the plurality of processes to obtain a combined financial loss (A8) arising from the future threat activity. (B9; B11; B15; B17)
30. The non-transitory computer readable medium of claim 29, wherein the computer program, when executed by the computer system, causes the computer system to include at least two modules including a first module configured to predict future threat activity and to output the predicted future threat activity to a second module. (A1; A2; A4)
15/012,182 Apparatus and method for assessing financial loss from cyber threats capable of affecting at least one computer network 2016
1. An apparatus including one or more computer processors and a computer readable memory in which programming code is stored, wherein the one or more computer processors are configured pursuant to programming code in the computer readable memory to predict, for each of a plurality of threats capable of affecting at least one computer network in which a plurality of systems operate, (B6) future threat activity using a Monte Carlo method based on stochastic modeling of past observed threat events, (B15; B18) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses, (A1; A2) (B1; B4; B14; B16)
wherein the one or more computer processors (A4) are configured, for a given threat, to model a set of past observed threat events (B14; B16) to obtain an estimate of at least one model parameter, and, in a Monte Carlo simulation of a given threat, (A6)
to predict future threat events (B4; B9; B11; B17) using the at least one model parameter and a stochastic model using a projection of at least one model parameter which is based on the estimate of at least one model parameter and on a randomly-drawn variable, and (A6)
to predict a distribution of future threat events by repeating the simulation using a plurality of variables. (A6) (B15)
2. The apparatus according to claim 1, wherein the apparatus is further configured to determine expected downtime of each of said systems (A7) (B7; B10) in dependence upon said predicted future threat activity and to determine financial loss for each of a plurality of operational processes (A7) (B12) dependent on the downtimes of each of said systems and to add financial losses for said plurality of processes so as to obtain a combined financial loss arising from the predicted future threat activity. (A8) (B9; B11; B15; B17)
3. The apparatus according to claim 1, wherein the apparatus is configured to model a set of past observed threat events (B1) so as to obtain at least one model parameter, B15) wherein at least one model parameter includes at least one parameter indicating goodness of fit of the model, using regression, weighted regression, linear regression, exponential regression, at least two different models, and (A6) (B18)
to obtain at least two different sets of model parameters. (A6)
4. The apparatus according to claim 1, comprising a user interface which is configured to;
present at least one model parameter to a user
present an outcome of stochastic modeling to a user, and to
display at least one of the financial losses and the combined financial loss on a display device. (A4; A6)
5. The apparatus according to claim 1, further comprising a user interface which is configured to present a
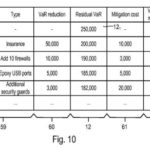
list of a plurality of risk mitigation measures (B3; B9)
corresponding value of the reduction in financial loss associated with implementing the measure
residual value at risk (B3; B9)
cost of implementing the risk mitigation action, (B3; B9) and
the ratio of the reduction and implementation cost on a display device. (A10)
6. The apparatus according to claim 1, wherein the apparatus is configured to:
predict future threat events using at least one model parameter and
a stochastic model using said at least one model parameter (B17) randomly draw at least one variable according to a predefined distribution and
use said at least one variable in the stochastic model
predict a distribution of future threat events using a Monte Carlo method by repeating a simulation, (B15; B17) and
allow for parameter uncertainty. (A6)
7. The apparatus according to claim 1, wherein the apparatus is configured to store at least one of the financial losses and the combined financial loss in a storage device. (A6)
8. The apparatus according to claim 1, wherein loss is expressed as:
value at risk (B3)
expected financial loss, and B9; B11; B15; B17)
a priori insurance risk premium value B9; B11; B15; B17)
9. The apparatus according to claim 1, wherein the apparatus is configured to retrieve a list of past observed threats (A1; A2) (B1; B2; B14; B16)
to determine the predicted future threat activity based upon the list of past observed threats, (A5) (B4;) and;
to output the predicted future threat activity to a firewall. (A2) (B2)
10. The apparatus according to claim 1, wherein the past observed list of threats includes, for each threat information, identifying at least one system, (A5A) (B1; B5; B6) and
frequency of occurrence of the threat. (A5A) (B1; B4; B8; B14; B16)
11. The apparatus according to claim 1, wherein the frequency of occurrence of the past observed threat includes at least one period of time, and
corresponding frequency of occurrence for the at least one period of time. (A5A) (B1; B4; B8; B14; B16)
12. The apparatus according to claim 1, wherein the one or more processors is configured pursuant to programming code to provide at least two modules including
a first module configured to predict future threat activity (B9; B11; B14; B17) using a Monte Carlo method, (A6) (B15; B18) and to output the predicted future threat activity to a second module. (A4)
13. A computer-implemented method, the method being performed by a computer system having one or more computer processors and a computer readable memory in which programming code is stored, whereupon execution of the programming code by one or more computer processors the computer system performs operations comprising:
predicting, (B9; B11; B14; B17) for each of a plurality of threats, future threat activity using a Monte Carlo method based on stochastic modeling of past observed threat events (B15; B18) capable of affecting at least one computer network in which a plurality of systems operate, wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses; (A1; A2) wherein for each given threat the method comprises;
modeling a set of past observed threat events (B14; B16) to obtain an estimate of at least one model parameter;
performing a Monte Carlo simulation of the given threat by:
predicting future threat events (B9; B11; B14; B17) using the at least one model parameter and a stochastic model using a projection of at least one model parameter (B18) which is based on the estimate of at least one model parameter and on a randomly-drawn variable, (B17) and
predicting a distribution of future threat events by repeating the simulation using a plurality of variables. (A6) (B17)
14. The method according to claim 13, further comprising
determining expected downtime of each system (A7) (B7; B10) in dependence upon said predicted future threat activity
determining financial loss for each of a plurality of operational processes (A7) (B12) dependent on the downtimes of the systems
adding losses for the plurality of processes to obtain a combined financial loss (A8) (B9; B11; B15; B17) arising from the future threat activity.
15. The method according to claim 13, wherein the predicting threat activity based on stochastic modeling of past observed threat events (B14; B16) includes
modeling a set of past observed threat events so as to obtain at least one model parameter, (B18) and
predicting future threat events using at least one model parameter and a stochastic model using said at least one model parameter. (A6) (B18)
16. A computer readable medium having a computer program thereon, which when executed by a computer system having one or more computer processors and a computer readable memory, causes the computer system to predict, for each of a plurality of threats, future threat activity (B9; B11; B14; B17) using a Monte Carlo method based on stochastic modelling of past observed threat events (B15; B18) capable of affecting at least one computer network in which a plurality of systems operate, (A6) wherein the plurality of threats includes a plurality of electronic threats and the plurality of electronic threats includes a plurality of computer viruses;
wherein execution of the computer program causes the computer system to perform, for each given threat, steps comprising:
modeling a set of past observed threat events to obtain an estimate of at least one model parameter; (B15)
performing a Monte Carlo simulation of the given threat (B15; B18) by:
predicting future threat events using the at least one model parameter and a stochastic model using a projection of at least one model parameter which is based on the estimate of at least one model parameter and on a randomly-drawn variable, (B4; B11; B17) and
predicting a distribution of future threat events by repeating the simulation using a plurality of variables. (A6) (B4; B11; B17)
17. The method of claim 13, in which the computer system includes at least two modules, wherein the method further comprises:
using a first module to predict future threat activity (A5A) and to output the predicted future threat activity to a second module. (A4)
18. The computer readable medium of claim 16, wherein the computer program, when executed by the computer system, causes the computer system to include at least two modules including a first module configured to predict future threat activity (B9; B11; B14; B17) and to output the predicted future threat activity to a second module. (A5A; A4)
15/696,202 Assessing and managing cyber threats 2017
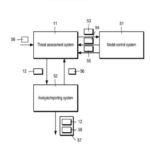
1. A system comprising:
one or more computers comprising one or more hardware processors; one or more computer-readable media storing instructions that, when executed by the one or more computers, cause the one or more computers to perform operations comprising:
receiving, by the one or more computers, data indicating a list of observed computer-based threats (B1; B2) including at least one selected from the group consisting of a virus, malware, a network intrusion, and a denial of service attack, (A1; A2) with data for each threat identifying frequency of occurrence, (A1; A2) (B1; B4; B8; B14; B16) which may include at least one period of time and corresponding frequency of occurrence for a given time window having a beginning and end; (A5A) (B1; B14; B16)
accessing, by the one or more computers, data specifying relationships between:
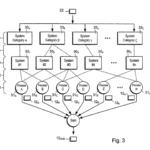
(i) IT system infrastructures representing computing devices of an organization and a network connecting the computing devices (B6; B7) and their physical and logical location, (B12) defined by information such as identity, name and category identity; (A3) (B1; B6; B8)
(ii) system categories indicating characteristics of assets of the organization; (A3) (B6; B7)
(iii) operational processes of an organization, (A3) defined by identity, a name and a value in terms of a monetary value for a given time window having a beginning and end; (A5A) (B6; B7; B9; B12)
(iv) mitigating actions representing the threat mitigation measures of the organization; (A10) (B3)
performing, by the one or more computers a plurality of simulations using a Monte Carlo method (A6) (B15; B17) using the accessed data specifying relationships (A4) (B1; B6; B8) to predict a distribution of threat events, (B15) each simulation involving propagating data through stochastic modelling (A6) for a given time window having a beginning and end; (A5A)
modelling threat events using at least two different stochastic models and obtaining at least two different sets of model parameters, (A6) (B18)
sampling, by the one or more computers, outcomes of the plurality of simulations generated using a Monte Carlo method (A6) according to the set of threat events within a series of temporal profiles, each having a beginning and end; (A5A) (B1)
sampling, by the one or more computers, a plurality of simulation outcomes of the plurality of simulations generated using a Monte Carlo method (A6) (B15; B17) that include mitigating actions representing the threat mitigation measures of the organization (A10) (B3) for a series of given time windows, each having a beginning and end;
based on the sampled outcomes of the simulations, determining, by the one or more computers, measures of impact of the computer-related threats to the organization (A7) (B7; B8; B10) for a given time window having a beginning and end and providing, by the one or more computers and for output to a user, graphical representations of the determined measures of impact of the computer-based threats to the organization, for a given time window having a beginning and end, in a graphical user interface; (A6) (B3; B9; B11; B12; B15; B17)
the one or more computers further configured to;
receive observed computer-based threat data; (A1; A2) (B1)
receive input data of the number of viruses contracted by period and the number of new viruses worldwide; (B2)
extrapolating from the input data, using a Monte Carlo method, to predict future computer-based threat activity rates and types (A6) (B4; B17) and;
outputting said predicted future computer-based threat activity into the network and firewall logs, updating the firewall policy tree to define the action of accept or deny, according to the changes automatically made to the policy tree of rules in the sets of firewall rules, which in turn inserts updated rules into the firewall policy. (A2) (B2)
2. The system of claim 1, wherein determining the measure of impact of the computer-based threats comprises determining a confidence interval for losses of the organization due to computer-based threats. (A6) (B15)
3. The system of claim 1, wherein each system category has an amount of value assigned; (B3; B6)
wherein performing the plurality of simulations comprises, for each of the plurality of the simulations, determining, based on parameters assigned to the computer-based threats and the mitigation actions, (B3; B19; B20) whether at least one of the computer-based threats is successful in accessing the system categories; (A5B)
wherein sampling outcomes of the plurality of simulations comprises, for each simulation, determining a combined amount of value for the system categories (A7; A8) (B9; B11; B15; B17) that were determined to be accessed by the computer-based threats during the simulation.
4. The system of claim 1, wherein performing the plurality of simulations and sampling outcomes comprise performing Monte Carlo simulations. (A6) (B15; B17)
5. The system of claim 4, wherein the Monte Carlo simulations are conducted to determine a distribution of a total value that may be lost to the threats (6) represented by the computer-based threats for a given time window having a beginning and end. (B15; B17)
6. The system of claim 1, wherein the operations further comprise:
model a set of threat events using at least two different models and obtain at least two model parameters; (B18)
determining the goodness of fit of the model for each model parameter; predict threat events using at least one model parameter; (B15)
determining predicted threat activity based on stochastic modeling of threat events; (B17)
randomly draw at least one variable according to a predefined distribution and use at least one variable in the stochastic model; (A6) present at least one model parameter to a user in a graphical user interface. (A6) (B18)
7. The system of claim 1, wherein a system category may be omitted so the computer-based threats will be considered directly. (A3)
8. The system of claim 1, wherein the Monte Carlo model represents a conditional probability distribution of each random variables is time-dependent for a discrete time index, and values (B15) determined for at least some of the system categories are conditioned on
(i) the values of the system category’s parents at a current time index, (B6; B7; B8) and
(ii) values determined for the system category for one or more prior time indexes.
9. A method performed by one or more computers, the method comprising:
receiving and accessing, by the one or more computers, data specifying relationships between:
(i) IT system infrastructures representing computing devices of an organization and a network connecting the computing devices and their physical and logical location, defined by information such as identity, name and category identity; (B1; B6; B8)
(ii) system categories indicating characteristics of assets of the organization; (B6; B7)
(iii) operational processes of an organization, defined by identity, a name and a value in terms of a monetary value for a given time window having a beginning and end; (A3) (B6; B7; B9; B12)
(iii) a list of observed computer-based threats (A1; A2) (B1) including at least one selected from the group consisting of a virus, malware, a network intrusion, and a denial of service attack, with data for each threat identifying frequency of occurrence, (B1; B4; B8; B14; B16) which may include at least one period of time and corresponding frequency of occurrence for a given time window having a beginning and end;
(iv) mitigating actions representing the threat mitigation measures of the organization; (A10) (B3; B19; B20)
the one or more computers performing a plurality of simulations using a Monte Carlo method (A6) (B15; B17) using the accessed data specifying relationships, (A3) (B1; B6; B8) each simulation involving propagating data through stochastic modeling for a given time window having a beginning and end; (A6)
sampling by the one or more computers, outcomes of the plurality of simulations generated using a Monte Carlo method, for a given time window having a beginning and end; (B15; B17)
sampling by the one or more computers, outcomes of the plurality of simulations generated using a Monte Carlo method, (A6) that include mitigating actions representing the threat mitigation measures of the organization (A10) for a given time window having a beginning and end; (B3; B19; B20)
performing, based on the sampled outcomes of the simulations generated using a Monte Carlo method, determining, by the one or more computers, measures of impact (A7) (B7; B8; B10) of the computer-related threats to the organization for a given time window having a beginning and end and providing, by the one or more computers and for output to a user, graphical representations of the determined measures of impact of the computer-based threats to the organization, for a given time window having a beginning and end, in a graphical user interface; (A6) (B3; B9; B11; B12; B15; B17)
receive observed computer-based threat data; (A1; A2) (B1; B14)
receive input data of the number of viruses contracted by period and the number of new viruses worldwide; (B2 B4; B8)
extrapolating from the input data, using a Monte Carlo method, to predict future computer-based threat activity rates and types (A6) (B4; B17) and;
outputting said predicted future computer-based threat activity to one or more firewalls, to improve accuracy in identifying computer based threats on the one or more computer networks, strengthen their accuracy through the detection of anomalous firewall policy rules, into the network and firewall logs, updating the firewall policy tree to define the action of accept or deny, according to the changes automatically made to the policy tree of rules in the sets of firewall rules, which in turn inserts updated rules into the firewall policy, (A2) (B2)
wherein the method is performed by one or more computers comprising one or more hardware processors; one or more computer-readable media storing instructions that, when executed by the one or more computers, cause the one or more computers to perform operations comprising.
10. The method of claim 9, wherein determining the measure of impact of the computer-based threats comprises determining a confidence interval for losses of the organization (A6) (B15) due to computer-based threats.
11. The method of claim 9, wherein each system category has an amount of value assigned; (A5A) (B3; B6)
wherein performing the plurality of simulations comprises, for each of the plurality of the simulations, determining, based on parameters assigned to the computer-based threats and the mitigation actions, (A10) (B3; B19; B20) whether at least one of the computer-based threats is successful in accessing the system categories;
wherein sampling outcomes of the plurality of simulations comprises, for each simulation, determining a combined amount of value (A8) (B9; B11; B15; B17) for the system categories that were determined to be accessed by the computer-based threats during the simulation.
12. The method of claim 9, wherein performing the plurality of simulations and sampling outcomes comprise performing Monte Carlo simulations. (A6) (B15; B17)
13. The method of claim 12, wherein the Monte Carlo simulations are conducted to determine a distribution of a total value that may be lost to the threats represented by the computer-based threats (A8) (B15; B17) for a given time window having a beginning and end.
14. The method of claim 9, wherein the operations further comprise:
model a set of threat events using at least two different models and obtain at least two model parameters; determining the goodness of fit of the model for each model parameter; predict threat events using at least one model parameter; determining predicted threat activity based on stochastic modeling of threat events; randomly draw at least one variable according to a predefined distribution and use at least one variable in the stochastic model; (B15; B17; B18)
present at least one model parameter to a user in a graphical user interface. (A6) (B18)
15. The method of claim 9, wherein a system category may be omitted so the computer-based threats will be considered directly. (A3)
16. The method of claim 9, wherein the Monte Carlo model represents a conditional probability distribution of each random variables is time-dependent for a discrete time index, (B6; B7; B8) and values (B15) determined for at least some of the system categories are conditioned on
(i) the values of the system category’s parents at a current time index, (B6; B7; B8) and
(ii) values determined for the system category for one or more prior time indexes.
17. A non-transitory computer-readable medium storing instructions that, when executed by the one or more computers, cause the one or more computers to perform operations comprising:
receiving and accessing, by the one or more computers, data specifying relationships between:
(i) IT system infrastructures representing computing devices of an organization (B6; B7) and a network connecting the computing devices and their physical and logical location, (B10; B12) defined by information such as identity, name and category identity; (B6; B7; B19)
(ii) system categories indicating characteristics of assets of the organization;
(iii) operational processes of an organization, defined by identity, a name and a value in terms of a monetary value for a given time window having a beginning and end; (A3) (B6; B7)
(iv) a list of observed computer-based threats (B1; B2) including at least one selected from the group consisting of a virus, malware, a network intrusion, and a denial of service attack, with data for each threat identifying frequency of occurrence, (A1; A2; A5A) (B1; B4; B8; B14; B16) which may include at least one period of time and corresponding frequency of occurrence for a given time window having a beginning and end;
(iv) mitigating actions representing the threat mitigation measures of the organization; (A10) (B3; B19; B20) the one or more computers performing a plurality of simulations using a Monte Carlo method, (A6) (B15; B17)each simulation involving propagating data through stochastic modeling (A6) for a given time window having a beginning and end;
sampling by the one or more computers using the accessed data specifying relationships, outcomes of the plurality of simulations for a given time window having a beginning and end;
sampling by the one or more computers using the accessed data specifying relationships, outcomes of the plurality of simulations (B15; B17) that include mitigating actions representing the threat mitigation measures of the organization (A10) (B3; B19; B20) for a given time window having a beginning and end;
based on the sampled outcomes of the simulations, determining, by the one or more computers, measures of impact of the computer-related threats to the organization (B7; B8; B10) for a given time window having a beginning and end and providing, by the one or more computers and for output to a user, graphical representations of the determined measures of impact of the computer-based threats to the organization, for a given time window having a beginning and end, in a graphical user interface; (A4; A6) (B3; B9; B11; B12; B15; B17)
the one or more computers further configured to;
receive observed computer-based threat data; (A1; A2) (B1; B14)
receive input data of the number of viruses contracted by period and the number of new viruses worldwide; (B2)
extrapolating from the input data, using a Monte Carlo method, to predict future computer-based threat activity rates and types (A6) (B4; B17) and;
outputting said predicted future computer-based threat activity to one or more firewalls, to improve accuracy in identifying computer based threats on the one or more computer networks, strengthen their accuracy through the detection of anomalous firewall policy rules, into the network and firewall logs, updating the firewall policy tree to define the action of accept or deny, according to the changes automatically made to the policy tree of rules in the sets of firewall rules, which in turn inserts updated rules into the firewall policy. (A2) (B2)
18. The non-transitory computer-readable medium of claim 17, wherein determining the measure of impact of the computer-based threats comprises determining a confidence interval for losses of the organization (A6; A9) (B15) due to computer-based threats.
19. The non-transitory computer-readable medium of claim 17, wherein each system category has an amount of value assigned; (B3; B6)
wherein performing the plurality of simulations comprises, for each of the plurality of the simulations, determining, based on parameters assigned to the computer-based threats and the mitigation actions, whether at least one of the computer-based threats is successful in accessing the system categories; (A5A; A5B)
wherein sampling outcomes of the plurality of simulations comprises, for each simulation, determining a combined amount of value (A8) (B9; B11; B15; B17) for the system categories that were determined to be accessed by the computer-based threats during the simulation.
20. The non-transitory computer-readable medium of claim 17, wherein performing the plurality of simulations and sampling outcomes comprise performing Monte Carlo simulations. (A6) (B15; B17)
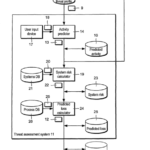
16/129,820 Valuing cyber risks for insurance pricing and underwriting using network monitored sensors and methods of use 2018
1. A system, comprising:
one or more networks comprising computing systems that are subject to a security policy, (A1; A2) the security policy comprising breach parameters defining one or more events that are indicative of an electronic threat, the security policy breach parameters being associated with a remediation provision in one or more network security devices policies for the computing systems and the network or networks;
one or more data collecting devices, deployed within the network or networks, that collect entity information and monitor network data of the network or networks that is related to security information; (A1; A2) (B1; B2; B14; B16)
one or more data collecting devices deployed outside the security perimeter, between the public network or networks and the one or more private networks, configured to collect electronic threat and security information from at least publicly accessible information and to monitor inbound network data; (A1; A2) (B1; B2)
samples network data and automatically detects occurrence of one or more of the events that are indicative of an electronic threat based on the network data;
identifies said electronic threat, or threats by cross-referencing data in the said collected publicly accessible electronic threat and security information, to confirm, or infer, that the network data monitored contains indicative types of electronic threats and by using a list of known threats stored in a database; (A1; A2) (B2)
produces an observed electronic threat profile, including at least, for each electronic threat, an identifier, a name, a description of the threat, specifying frequency of occurrence of each threat within a time block, a target, or targets, for each threat and a severity score for each target (B1; B1; B2; B14) and stores the data in a database accessed by a threat assessment system (A1; A2) that;
extrapolates predicted future electronic threat profiles (A5A) (B4; B17) from the observed electronic threats and collected security information, in combination with the electronic threat profiles using stochastic modeling (A6) (B17; B18) and;
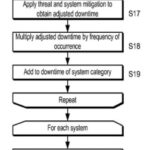
automatically determines the breach parameters that apply for the one or more electronic threats that have been identified; (B1; B6; B7; B8; B9; B15)
automatically outputting predicted future electronic threat profiles to network and network security device logs, updating the network security device policy tree of rules in the sets of network security device rules; (A2) (B2) and
generates a remediation of the one or more network security devices security parameters (A2) (B2; B19; B20) for the network or networks based upon predicted losses arising from the observed electronic threats.
2. The system according to claim 1, wherein the network data collected comprises at least publicly available information (B2) used to obtain direct, or indirect information regarding an entity having assets of a network infrastructure and business processes dependent upon said network assets or sub-assets.
3. The system according to claim 1, wherein the collected direct or indirect information is evaluated for that having an impact on the risk posed to the entity, by cross-referencing data in the collected information (A1; A2) to confirm, or infer, that the entity is referenced in the said electronic threat data according to the network infrastructure assets and targets of the said electronic threats. (B1; B2; B9; B10)
4. The system of claim 1, wherein the threat analyzer and threat assessment systems are configured to evaluate network data and traffic (A1; A2) (B1; B2) from the at least publicly accessible information and the monitored inbound network data.
5. The system according to claim 4, wherein the network data is evaluated by cross-referencing the network data against a list of known electronic threats stored in a database (A1; A2) (B1; B2) and the collected publicly accessible data for any security-related information, including an identifier, a name, a description of the threat, a temporal profile specifying the frequency of occurrence of the electronic threat, the number of new viruses in the wild, a target, or targets of the electronic threat and a severity score for each electronic threat.
6. The system according to claim 5, wherein the threat assessment system is further configured to:
receive observed electronic threat data, (B1) collected electronic threat and security information from at least publicly accessible information (B2) and monitored inbound network data, (A1; A2) (B2) the number of new viruses in the wild for a specified time period; and
extrapolate future threat event frequency (B4; B11; B17) and produce a profile of predicted threat activity, (A5A) which includes a list of predicted electronic threats and their expected frequency of occurrence and a severity score and store the profile in a database. (A5A) (B2; B18)
7. The system according to claim 1, wherein the threat analyzer comprises a first set of sensors that operate on a data link layer of the network or networks. (A1)
8. The system according to claim 7, wherein the threat analyzer further comprises a second set of sensors that operate on an Internet Protocol Address layer of the network or networks. (A1)
9. The system according to claim 8, wherein the second set of sensors transmits the network data information (B1) to the first set of sensors for storage in one or more databases.
10. The system according to claim 1, wherein the remediation comprise s feedback to one or more network security devices, automatically outputting predicted future electronic threat profiles to the entity’s network and network security device logs, updating the network security device policy tree of rules in the sets of network security device rules; (A2) (B2)
automatically inserting the updated network security device rules into the network security device policy to generate a remediation of the said network security device for the private network or networks for improvement to the operation of the one or more network security devices based on the nature of the one or more electronic threat events that occurred and the predicted future electronic threats. (A2) (B2)
11. The system according to claim 1, wherein the threat assessment system is further configured to query the entity, collected electronic threat and security information from at least publicly accessible information, network or networks for information relating to predicted electronic threat activity, (B2) systems within the network or networks, business processes using the network or networks. (B4; B6; B7; B8; B14)
12. The system according to claim 1, wherein the threat assessment system is further configured to utilize the entity information, collected electronic threat and security information from at least publicly accessible information, and network data to calculate a composite score from predicted activity that is indicative of a volume of electronic threats that may cause a cyber security risk for the entity (B2; B14; B16) and a threat profile that is indicative of an electronic threat level of sophistication electronic threats. (A5A) (B1)
13. The system according to claim 12, wherein the threat assessment system is further configured to:
evaluate a plurality of networks to generate a plurality of predicted electronic threat activity values, a plurality of system risk values, a plurality of business process risk values and a plurality of predicted loss values, (A5A; A5B; A6; A7; A8) the plurality of networks comprising one or more networks; and
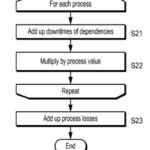
plot the plurality of predicted electronic threat activity values, the plurality of system risk scores, the plurality of business process risk values and the plurality of predicted loss values graphically. (A6) (B3; B9; B10; B11; B12; B15)
14. The system according to claim 12, wherein the threat assessment system is further configured to calculate the effect of a mitigation action upon the predicted loss values (A10) (B3; B19; B20) that correspond to changes to one or more assets and or sub-assets to the network infrastructure.
15. The system according to claim 12, wherein the threat assessment system is further configured to output the effect of one or more mitigation actions, alone or in combination, upon the predicted loss values that correspond to changes to one or more assets and or sub-assets within the one or more network infrastructures on a display device. (A6; A9; A10) (B3; B6; B7; B8; B9; B10; B11; B12; B15; B19; B20)
16. A method, comprising:
establishing security parameters for an entity, the security parameters defining one or more events that are indicative of an electronic threat, the security policy breach parameters being associated with a remediation provision in a one or more network security devices policies of the entity:
collecting entity information and monitor network data of the network or networks that is related to security information; (A1; A2) (B1; B2; B14; B16)
collecting electronic threat and security information from at least publicly accessible information and monitoring inbound network data; (A1; A2) (B1; B2)
sampling network data and automatically detecting occurrence of one or more of the events that are indicative of an electronic threat based on the network data;
identifying said electronic threat, or threats by cross-referencing data (A1; A2) in the said collected publicly accessible electronic threat and security information, to confirm, or infer, that the network data monitored contains indicative types of electronic threats and by using a list of known threats stored in a database; (A1; A2) (B2)
producing an observed electronic threat profile, (A5A) including at least, for each electronic threat, an identifier, a name, a description of the threat, specifying frequency of occurrence of each threat within a time block, a target, or targets, for each threat and a severity score for each target (B1; B2; B14) and storing the data in a database accessed by a threat assessment system that;
extrapolating predicted future electronic threat profiles from the observed electronic threats and collected security information, (A5A) in combination with the electronic threat profiles using stochastic modeling; (A6) (B17; B18)
automatically determining the breach parameters that apply for the one or more events that occurred; (B1; B6; B7; B8; B9; B15)
automatically outputting predicted future electronic threat profiles to network and network security device logs, updating the network security device policy tree of rules in the sets of network security device rules; (B2) and
causing a remediation of network security device security parameters determined based upon predicted losses arising from electronic threats. (A2) (B2; B19; B20)
17. The method according to claim 16, further comprising feedback to one or more network security devices, for improvement to the operation of the one or more network security devices based on the nature of the one or more electronic threat events that occurred and the predicted future electronic threats. (A2) (B2)
18. The method according to claim 17, further comprising tying at least one or a combination of predictive activity values, system risk values, business process risk values and changes to predicted loss values to remediation adjustments. (A7; A10) (B3; B19; B20)
19. The method according to claim 16, wherein the remediation comprises one or more changes, individually or in combination, to a network infrastructure, hosting infrastructure, website topology, I.T. systems, business processes, content distribution networks, shared hosting, cloud services, patching, updating, default passwords, and any combinations thereof. (B2; B3; B6; B7; B8)
20. A system, comprising:
one or more data collecting devices deployed within a network that collect entity information and monitor network traffic of the network that is related to security information, one or more data collecting devices deployed outside the security perimeter, between the public network or networks and the one or more private networks, configured to collect electronic threat and security information from at least publicly accessible information and to monitor inbound network data; (A1; A2) (B1; B2)
samples network data and automatically detects occurrence of one or more of the events that are indicative of an electronic threat based on the network data;
identifies said electronic threat, or threats by cross-referencing data (A1; A2) in the said collected publicly accessible electronic threat and security information, to confirm, or infer, that the network data monitored contains indicative types of electronic threats and by using a list of known threats stored in a database; (A1; A2) (B1; B2)
produces an observed electronic threat profile, (A5A) including at least, for each electronic threat, an identifier, a name, a description of the threat, specifying frequency of occurrence of each threat within a time block, a target, or targets, for each threat and a severity score for each target (B1; B2; B14) and stores the data in a database accessed by a threat assessment system that;
extrapolates predicted future electronic threat profiles (A5A) (B4; B17) from the observed electronic threats and collected security information, in combination with the electronic threat profiles using stochastic modeling; (B17; B18)
the network comprising computing systems that are subject to a security policy, the security policy comprising breach parameters defining one or more events that are indicative of an electronic threat, the breach parameters being associated with a remediation provision in one or more network security devices policies for the computing systems and the network or networks; (B2)
a threat analyzer and threat assessment system; (A1; A2)
automatically detects occurrence of one or more of the events that are indicative of an electronic threat based on the network traffic;
automatically determines the breach parameters that apply for the one or more electronic threats that have been identified; and
generates a remediation of the one or more network security devices security parameters for the network or networks based on predicted losses arising from the observed electronic threats. (A1; A2) (B2)
16/094,617 System and method for extracting and combining electronic risk information for business continuity management with actionable feedback methodologies 2020
1. A system, comprising:
one or more networks comprising computing systems, a threat assessment system, a system risk calculator, an activity predictor, a predicted loss calculator, a model control system and an analysis and reporting system, (A1; A2) comprised of one or more processors and memory communicatively coupled with the processor and or processors, the memory storing instructions; (A4)
one or more computer agents deployed within a demilitarized zone between a public network, or networks and a private network, or networks, (A1; A2) configured to collect electronic threat and security data from at least publicly accessible information and to monitor network data transmitted via a public network, or networks, to a private network, or networks; (B1; B2)
receiving, by the activity predictor, observed electronic threat data and collected security data to extrapolate future electronic threat event frequency (A5A) using stochastic modeling, (A6) (B17; B18) using polynomial regression to create distributions from the said electronic threat activity prediction and producing one or more profiles of predicted electronic threat activity, producing an electronic threat profile, (A5A) including at least, for each electronic threat, an identifier, a name, a description of the threat, the frequency of occurrence of each electronic threat within a time block, a target or targets, for each threat and a severity score for each target; (A5A; A5B) (B1; B2; B4; B14; B16)
determining a time profile for each target of the one or more electronic threats, each time profile defined in terms of one or more time blocks and the number of successful electronic threats expected in each time block;
receiving, by the system risk calculator, the one or more predicted electronic threat profiles, information about the I.T. systems and the categories to which they belong from a systems database (A2) (B6; B7; B8) and produces a risk profile to the systems expressed as predicted downtime over a given period, determining downtime for a system category (A7) based on the expected damage level for a successful electronic threat; (B7; B10)
summing by the system risk calculator downtimes of dependencies of the system categories (A7) on which systems depend and, or the dependencies of the system categories on which system dependencies depend; (B9; B11; B15; B17)
receiving by the predicted loss calculator, system risk and data listing operational businesses processes from a database, (A2) (B2; B6; B7; B8) to predict loss for each operational business process, (A5A) aggregating the results for each operational business process, (A8) (B9; B11; B15; B17)outputting predicted loss data to be stored in a database and, or to a display device; (A6)
adding up, by the predicted loss calculator, for each operational business process, the predicted downtimes of the system categories on which each operational business process depends, determining a duration for which the operational business process is unavailable and multiplying the duration by a value of the operational business process to quantify loss; (A8) (B9; B11; B15; B17)
automatically outputting predicted future electronic threat profiles to network and network security device logs, updating network security device policy trees of rules in the sets of network security device rules; (B2)
automatically inserting the updated network security device rules into network security device policies generating feedback to network security device security parameters to improve the accuracy of false positive and false negative detection of the said network security devices. (A2) (B2)
2. The system of claim 1, wherein the quantified loss is stored for one or more given network configurations and compared with quantified loss values resulting from one or more simulated changes, using the model control system, (A9) to the network configuration, or one or more changes to network security device parameters, the resulting loss or range of losses and configurations being stored and, or displayed on a display device. (A9) (B3; B10; B12; B15; B17)
3. The system of claim 1, wherein the model control system controls the modeling process by instruction from a user and, or according to a predefined manner, confirming, setting and or passing model parameters for a given electronic threat to be stored and or used in predicting electronic threat activity and outputting simulations for any given electronic threat to the analysis reporting system and or a display device. (A9) (B18)
4. The system of claim 1, wherein the analysis and reporting system generates and or receives inputs or settings which are supplied to the threat assessment system, receives one or more values of quantified loss or losses, generating one or more reports which may include some, or all, of the values of quantified loss for the one or more given network configurations, the reduction in quantified risk values resulting from additional security measures, including the total cost of implementing the said additional security measures. (A9; A10) (B3; B11; B12)
5. The system of claim 1, further comprising generating a first value using one or more stochastic models assigned to each business process dependent upon the assets and or sub-assets of the private network infrastructure, representing a first level of assessed risk from the predicted electronic threat profile; (B18)
generating one or more additional values using one or more stochastic models assigned to each business process dependent upon the assets and or sub-assets of the private network infrastructure, representing a second or more levels of assessed risk from the predicted threat profile, higher or lower than the first value of assessed risk, based on one or more changes to at least one asset or sub-asset of the private network infrastructure. (A9; A10) (B15)
6. The system of claim 1, comprising specifying probability distributions for the number of electronic threat events and the impact of each of the said electronic threat events using a Poisson distribution for the number of electronic threat events and a lognormal distribution for the impact of the electronic threat events. (A6) (B15)
7. The system of claim 1, comprising calculating a potential total risk value arising from electronic threats in a future time block, by multiplying the number of successful electronic threat events, by an assumed loss value using sampling rates from the lognormal distribution and summing to attain a total risk value (A6; A8) for the current period. (B9; B11; B15; B17)
8. The system of claim 1, comprising the selection of model parameters by the model control system, the model control system confirming, setting, or passing model parameters for a given electronic threat and or threats to the threat assessment system and presenting the simulations for any given electronic threat and or threats to a user and repeating the process for one or more of the electronic threats, varying the model inputs according to a user predefined manner or according to user input. (A6; A9) (B2; B18)
9. The system of claim 1, comprising calculating a risk exposure value for a given configuration of a private network using the data acquired by the threat assessment system, modeling using the acquired electronic threat and security information data to extrapolate predicted future electronic threats, applying future predicted values to determine a fraction of electronic threats contracted, (A5A; A5B) recalculating the risk value after a simulated change to the configuration of the private network using the model control system (A6; A9) and presenting the one or more simulations to a user to determine a risk exposure value for risk transfer to mitigate the potential effects of the predicted electronic threats. (A6; A10) B11; B15; B17)
10. The system of claim 1, comprising generating or receiving by the analysis and reporting system, as a result of inputs or settings from a user, a report including all risk values, and other information such as metrics, to predict potential variability in loss values between one entity and another to provide inputs to pricing of risk transfer (A9; A10) (B11; B15; B17) for a given entity with a given configuration of private network and assets and or sub-assets of the said private network.
11. A method performed by one or more computers, the method comprising:
one or more networks comprising computing systems, a threat assessment system, a system risk calculator, an activity predictor, a predicted loss calculator, a model control system and an analysis and reporting system, comprised of one or more processors and memory communicatively coupled with the processor and or processors, the memory storing instructions;
one or more computer agents deployed within a demilitarized zone between a public network, or networks and a private network, or networks, configured to collect electronic threat and security data from at least publicly accessible information and to monitor network data transmitted via a public network, or networks, to a private network, or networks; (A1; A2) (B1; B2)
receiving, by the activity predictor, observed electronic threat data and collected security data (A1) to extrapolate future event frequency using stochastic modeling, (B17; B18) using polynomial regression (A6) to create distributions from the said electronic threat activity prediction and producing one or more profiles of predicted electronic threat activity, producing an electronic threat profile, including at least, for each electronic threat, an identifier, a name, a description of the threat, the frequency of occurrence of each electronic threat within a time block, a target or targets, for each threat and a severity score for each target; (A5A) (B1; B2; B4; B14; B16)
determining a time profile for each target of the one or more electronic threats, (A5A; A5B) each time profile defined in terms of one or more time blocks and the number of successful electronic threats expected in each time block;
receiving, by the system risk calculator, the one or more predicted electronic threat profiles, information about the I.T. systems and the categories to which they belong from a systems database (A1; A2) and produces a risk profile to the systems expressed as predicted downtime over a given period, determining downtime for a system category based on the expected damage level (A7) for a successful electronic threat; (B7; B10)
summing by the system risk calculator downtimes (A8) of dependencies of the system categories on which systems depend and, or the dependencies of the system categories on which system dependencies depend; (B9; B11; B15; B17)
receiving by the predicted loss calculator, system risk and data listing operational business processes from a database, (A2) (B2; B6; B7; B8) to predict loss for each operational business process, aggregating the results for each operational business process, (A8) (B9; B11; B15; B17) outputting predicted loss data to be stored in a database and, or to a display device; (A4; A6; A10)
adding up, by the predicted loss calculator, for each operational business process, the predicted downtimes of the system categories on which each operational business process depends, determining a duration for which the operational business process is unavailable and multiplying the duration by a value of the operational process to quantify loss; (A8) (B9; B11; B15; B17)
automatically outputting predicted future electronic threat profiles to network and network security device logs, updating network security device policy trees of rules in the sets of network security device rules; (B2)
automatically inserting the updated network security device rules into network security device policies generating feedback to network security device security parameters to improve the accuracy of false positive and false negative detection of the said network security devices. (A2) (B2)
12. The method of claim 11 wherein the quantified loss is stored for one or more given network configurations and compared with quantified loss values resulting from one or more simulated changes, using the model control system, to the network configuration, or one or more changes to network security device parameters, the resulting loss or range of losses and configurations being stored and, or displayed on a display device. (A4; A9) (B3; B10; B12; B15; B17)
13. The method of claim 11 wherein the model control system controls the modeling process by instruction from a user (A9) and, or according to a predefined manner, confirming, setting and or passing model parameters for a given electronic threat to be stored and or used in predicting electronic threat activity and outputting simulations for any given electronic threat to the analysis reporting system and or a display device. (A9) (B2; B18)
14. The method of claim 11 wherein the analysis and reporting system generates and or receives inputs or settings which are supplied to the threat assessment system, receives one or more values of quantified loss or losses, generating one or more reports which may include some, or all, of the values of quantified loss for the one or more given network configurations, the reduction in quantified risk values resulting from additional security measures, including the total cost of implementing the said additional security measures. (A9; A10) (B3; B11; B12)
15. The method of claim 11 comprising generating a first value using one or more stochastic models assigned to each business process dependent upon the assets and or sub-assets of the private network infrastructure, representing a first level of assessed risk from the predicted electronic threat profile; (B18)
generating one or more additional values using one or more stochastic models assigned to each business process dependent upon the assets and or sub-assets of the private network infrastructure, representing a second or more levels of assessed risk from the predicted threat profile, higher or lower than the first value of assessed risk, based on one or more changes to at least one asset of the private network infrastructure. (A9; A10) (B15)
16. The method of claim 11 comprising specifying probability distributions for the number of electronic threat events and the impact of each of the said electronic threat events using a Poisson distribution for the number of electronic threat events and a lognormal distribution for the impact of the electronic threat events. (A6) (B15)
17. The method of claim 11 comprising calculating a potential total risk value arising from electronic threats in a future time block, by multiplying the number of successful electronic threat events, by an assumed loss value using sampling rates from the lognormal distribution (A6) and summing to attain a total risk value for the current period. (A8) (B9; B11; B15; B17)
18. The method of claim 11 comprising the selection of model parameters by the model control system, (B2; B18) the model control system confirming, setting, or passing model parameters for a given electronic threat and or threats to the threat assessment system and presenting the simulations for any given electronic threat and or threats to a user and repeating the process for one or more of the electronic threats, varying the model inputs according to a user (A9) predefined manner or according to user input. (B2; B3; B6; B7; B8; B15; B17; B18; B19; B20)
19. The method of claim 11 comprising calculating a risk exposure value for a given configuration of a private network using the data acquired by the threat assessment system, (A3; A5A; A5B; A6; A7; A8) (B4; B9; B11; B12; B15; B17) modeling using the acquired electronic threat and security data to extrapolate predicted future electronic threats, applying future predicted values to determine a fraction of electronic threats contracted, recalculating the risk value after a simulated change to the configuration of the private network using the model control system (A9) (B4; B9; B11; B12; B15; B17) (and presenting the one or more simulations to a user to determine a risk exposure value for risk transfer to mitigate the potential effects of the predicted electronic threats. (A9; A10) (B11; B15; B17)
20. The method of claim 11 comprising generating or receiving by the analysis and reporting system, as a result of inputs or settings from a user, a report including all risk values, and other information such as metrics, to predict potential variability in loss values between one entity and another to provide inputs to pricing of risk transfer (A9; A10) for a given entity with a given configuration of private network and assets and or sub-assets of the said private network. (B4; B6; B8; B10; B11; B12; B14; B15; B16; B17; B19; B20)
