May 2021 delivered a major cyber attack on a major national infrastructure entity with a large percentage of a county’s population dependent upon it. Prior to this, a global technology corporation suffered a similar fate, with the Irish healthcare system being targeted shortly after the first two events.
In the case of the Colonial Pipeline cyber attack, the hacking group Darkside stated that they never intended to cause the negative social impact resultant from the lack of fuel across America. The group then made the claim that their sole objective was a financial one, that the group was agnostic with regard to politics and they would now implement a change to their organization to ensure all proposed attacks were signed off within the group prior to execution.
Can a hacker group claim to have a single motivation and that they both represent and control all the members within that organization? Something of a rhetorical question of course, but can this series of incidents within a short period of each other inform as to future attack trends?
The first hack occurred in 1963, with the objective of gaining free use of telephone systems and thus for financial advantage. The first network penetration attack took place in 2008 and shortly after, the first ransomware attack in 2009; again for financial advantage.
It would thus appear from the above and the recent attacks that types of cyber attack evolve in lockstep with technology evolution. However, when reviewing technology evolution and matching it against attack evolution the picture is less clear.
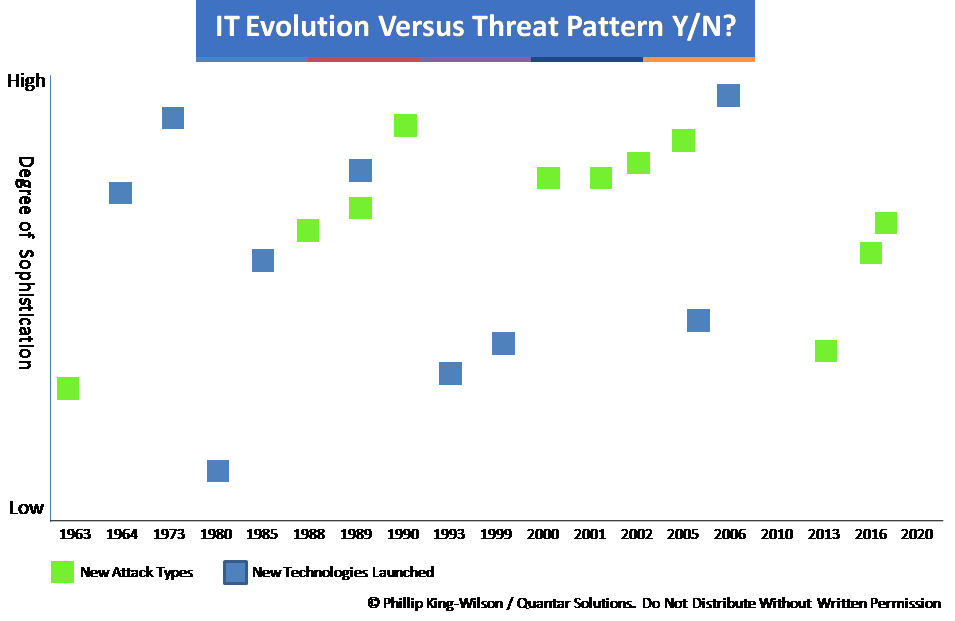
The ability to automate attacks and reduce the level of skill required by an attacker in successfully executing an attack is a more recent development. At the outset of modern computing, developers were working at machine code level, one’s and zero’s. What developed as computing grew was the number of available tools for developers to work more efficiently and faster, using compilers. The ability to use a high level programming language in conjunction with a compiler enabled code to be eventually written once and run in multiple environments.
As software has evolved, so have developer tools and over generations, the ability to work at base code level has been supplanted by the ability to write either client or server software in order to meet the continual demand growth. As technologies increase in complexity, so the number of full stack developers falls in percentage terms. The effect of this is an ability of hackers, with low to moderate skills to execute attacks successfully.
With the continued motivation of cyber attacks being for financial gain, attackers and would-be hackers have utilised the same software developer tools to create highly effective hacker toolkits that require little skill to use. With organized hacking groups such as Darkside running what it effectively a franchise model, instructions are provided alongside attack tools in exchange for a percentage of the ransoms paid.
We know that Colonial Pipeline paid $5 million, with Toshiba and the Irish Government not making any statements as to whether they paid or not (the Irish representative stated no ransom had been paid “as yet”). Individuals seeking financial gain have a path to potential wealth with few international cases against hackers being made.
Covid-19 has created an additional step-change, with remote working, forced rapid digitisation of entire sectors, with security practitioners being left behind the curve in respect of personnel resources in a market with a dearth of skilled professionals.
So returning to the original question of whether the recent major attacks inform as to future trends, personal financial gain will always be a human trait. With perceived likelihood of success versus the risk of being caught and imprisoned as it stands, the probability of attackers utilising the available technologies is very high. As we move into the realm of 5G (6G has been in development since 2019), AI, increased holographic use and VR, so the threat vectors increase and offer greater attack opportunities.
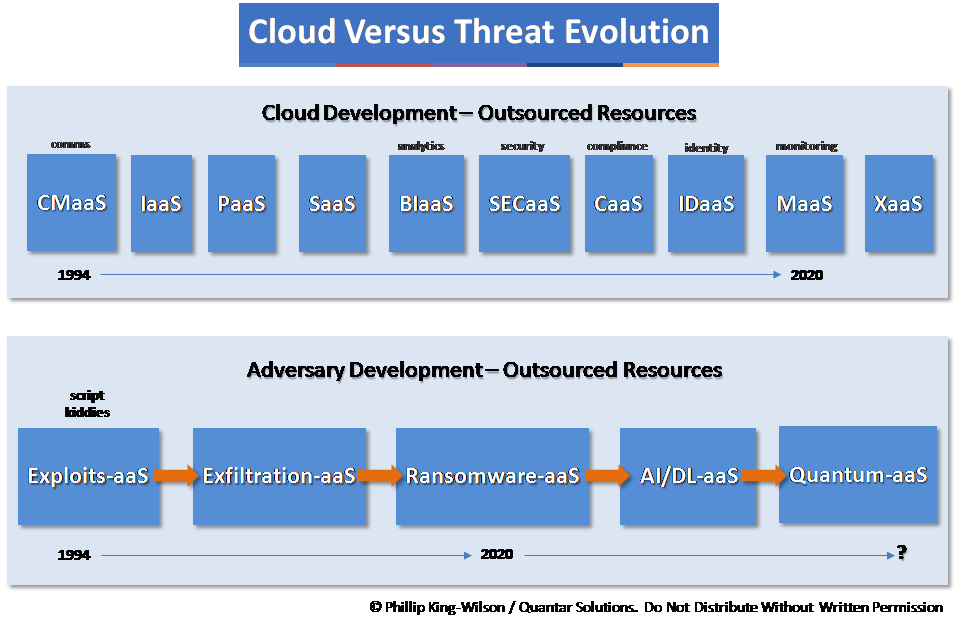
As we continue our path of ever-increasing dependence on computing and outsourcing to third parties, so we also continue to build upon unsound foundations for cyber attack resilience. The vision is clear: cyber attacks will proliferate as methods, targets, skill levels, ransom payouts as long as the current regulatory, enforcement and security capabilities of all countries lag behind highly motivated individuals and organized groups.
For more information on how Quantar can assist you in cyber risk management contact us.